The Monster in the Closet: Supply Chain Risk
- October 28, 2022
October coincides with the ‘spooky season’ in many countries, which can conjure scary stories about ghosts, headless horsemen and other things that can keep us awake at night. For those of us in cybersecurity, there are other scary stories that keep us awake at night throughout the year: the nefarious activities that make people’s devices, data and systems go bump in the night and day.
You’ve heard about the usual types of attacks – phishing emails, ransomware attacks and the like. Here’s the part that’s even more terrifying… even if you practice safe emailing and web surfing, you could already have malware infecting your device even before you boot up. That’s because malicious activities can happen in the manufacture of your computer if your original equipment manufacturer’s (OEM) supply chain practices are not as secure as they could be.
You may think of a supply chain as trucks rolling down the freeway or trains brimming with goods riding the rails. And yes, those are the traditional views of supply chain of things moving around the world. But in reality, today’s supply chain is complex and globally interconnected.
Because of its many touch points, the supply chain has become a major attack vector. For instance, 62 percent of network breaches were attributed to supply chain vulnerabilities, according to Verizon’s 2022 Data Breach Investigations Report.¹ PC hardware (the chips and motherboards) is at risk. So is firmware, the brains behind your machine. And let’s not forget about the physical security of the facilities and people. How do you reduce the opportunity for supply chain compromise? Make security part of your evaluation process every time you work with OEMs to procure devices. Keep in mind that your OEM’s supply chain is now your supply chain – and it’s in your best interests to work with OEMs that invest deeply in the security of their supply chain.
Dell not only builds security into its products – we build products securely. This covers the hardware, software and firmware used. Security starts with the design of the product, and Dell has a well-established Secure Development Lifecycle (SDL), which ensures security is built in from the initial concept. We prioritize investment in robust processes and controls embedded throughout our supply chain. In fact, supply chain security is a top priority for Dell. The strength of the Dell supply chain extends through numerous manufacturing locations, Dell factories, direct supplier factories of components and parts, as well as our original design manufacturer (ODM) partners.
In addition, our “second touch” operations sites provide value-added services for customers to match their unique needs. Every step of the way includes processes to ensure security and operating according to rigorous and documented quality management standards, which span assembly, software installation, functional testing and quality control.
 To ensure quality and security for the devices and components partners produce, Dell performs rigorous partner screening processes. Frequent and routine partner audits not only add to quality and security, but they also ensure compliance with comprehensive supply chain security standards developed and maintained by Dell. In addition to these standards, Dell device manufacturers frequently test parts to ensure counterfeit products do not make their way into the supply chain.
To ensure quality and security for the devices and components partners produce, Dell performs rigorous partner screening processes. Frequent and routine partner audits not only add to quality and security, but they also ensure compliance with comprehensive supply chain security standards developed and maintained by Dell. In addition to these standards, Dell device manufacturers frequently test parts to ensure counterfeit products do not make their way into the supply chain.
To further reduce risk, our processes feature a unique piece part identification number (PPID) and a label that is affixed with this information for specific high-risk components. This label contains information about the supplier, the part number, country of origin and date of manufacture. This allows Dell to identify, authenticate, track and validate these components to ensure the customer received what was ordered and shipped.
From a delivery perspective, our freight operations are protected by layers of physical security, with door-locking mechanisms and a variety of tracking devices designed to detect, which allow Dell to identify if devices have been tampered with in transit. Dell devices also feature tamper detection technologies, which provide an additional level of protection. Additional supply chain services are available to customers who are interested in even greater layers of security. These offerings include tamper-resistant seals and National Institute of Standards and Technology (NIST)-level hard drive wipes, which erase data, reducing concerns from IT admins regarding permanent removal of any previous data.
Another key piece of Dell supply chain security for our commercial devices features cryptographically signed platform certificates, which capture snapshot attributes of platforms during manufacturing, assembly testing and integration. These attributes are then cryptographically linked to the specific device using the trusted platform module (or TPM) as a hardware root of trust to ensure devices have not been tampered with. This capability, offered as Secured Component Verification (SCV), is available for customers in the federal sector with expanded availability soon.
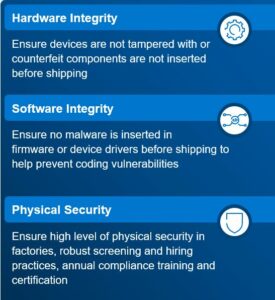
Dell supply chain procedures help to ensure the integrity of devices from all critical perspectives: hardware, software and physical integrity. Our hardware integrity ensures devices are not tampered with (e.g., counterfeit components are not inserted before shipping). Dell software integrity aims to help ensure no malware is inserted into the firmware or device drivers before shipping and prevents coding vulnerabilities. Physical security is at the highest level in both Dell direct and partner factories, with robust screening and hiring practices, annual compliance training and certification to ensure ongoing quality and security.
Our quality processes extend throughout the life of our products, with procedures that incorporate security in licensing, entitlements, and updates of everything, from software and firmware to patch management. It covers the device’s end-of-life, which is managed by Dell using responsible retirement policies, so that your data is protected when PCs are returned for refurbishment and recycling.
So, what monsters may be lurking across your supply chain? Remember, attackers only need one point of entry to inflict devastating damage. Prepare for the worst-case scenario. Visit Dell’s endpoint security solutions page or contact your Dell Sales Rep to learn more about the defenses built into our supply chain.
Read our Supply Chain Assurance whitepaper to learn more about the strict standards and integrity controls governing our supply chain.
Dell and Intel’s whitepaper Achieving Pervasive Security Above and Below the OS.
1Verizon 2022 Data Breach Investigations Report, registration required for download.